
Novus did an exceptional job coming through for us on such a tight schedule. I look forward to working with them again in the future. They’re one of the most capable technology organizations we’ve have had the pleasure of working with. They delivered.

GRAND SLAM!!!! Ryan and his team are fantastic and I am so happy I decided to move forward on this relationship. Wish I had done it a couple of months ago. Thank you for your guidance and patience in helping me understand and appreciate the intricacies involved in the challenge before all of us. Everything has exceeded my expectations.

With the incredible support we receive from Kevin & Cam, we are able to give our entire workforce the ability to work offsite. This was no small task and the Novus team really worked hard on our behalf. Thank you all!

I wanted to let you know how impressed I have been with the Novus team. They continue to meet my expectations, regularly exceeding them. I can’t thank you enough for all the support your team provided in Willington as we transitioned our students and staff to learning from home.

Having Novus and their expertise as part of our team has allowed us to consider various technology solutions that we didn’t even know existed.
Strategic Consulting
Technology changes introduce as many challenges as they do opportunities. To be well prepared for either, a structured and informed thought process is needed — in other words, a strategic technology plan. If crafted well, the plan will create the business case an organization should use to justify investment that directly supports the strategic goals and overall direction of the organization, while protecting critical data at the same time.
Our focus when working with clients to create a strategic technology plan includes:
- Understanding the organization’s key goals at both an operational and strategic level
- Assessing strengths and weaknesses with current IT infrastructure and cyber posture
- Assessing how critical data is managed, looking at the people, processes/workflows, and technology involved
- Eliciting employee feedback on ways technology is and isn’t making their jobs easier, plus what’s missing
- Defining the risk and opportunity cost of not making certain technology, cyber or data investments
- Determining the technology initiatives that best align with key operational and strategic goals and prioritizing them
- “Finding” money to fund high-priority initiatives by identifying where current technology spend can be better optimized
Technology Assessments
IT environments are continually changing. Unless sufficient attention is paid, problems can and will emerge — inefficiencies, performance issues, redundancies, security vulnerabilities, unintended data silos, etc. Eventually, it becomes difficult to determine what is and isn’t working well. When this happens, devoting IT resources and investment can become a guessing game.
Our clients prefer a different approach. Our technology assessments result in a report that reduces uncertainty by highlighting where attention and investment should be focused. We examine not only at the IT infrastructure level but also at the people and process level, where many of an organization’s “technology” weaknesses originate.
In addition to how employees use technology and how critical data is being managed, we also evaluate the underlying technology your organization is dependent on: network infrastructure, server infrastructure, data storage, desktop and other endpoint devices, backup systems, cloud services, business applications, disaster recovery & business continuity preparedness, network security and other risk factors, telephony, and document management.
Accurately and objectively self-assessing an organization’s own technology condition is nearly impossible. There is too much bias and that easily distorts reality. The value of an unbiased 2nd set of eyes cannot be overstated. Novus assumes this role for many organizations that have come to the realization an independent opinion is what is needed.
Cybersecurity Assessments
As a supplement to your organization’s self-assessment efforts, Novus offers a range of services that help with evaluating cybersecurity posture, achieving compliance requirements, and better adhering to partner and client security mandates.
Our assessment work extends well beyond optimizing cybersecurity in existing infrastructure. We evaluate more broadly, starting with the critical data an organization is dependent on to operate. Through a process of interviewing, software-enabled scanning, and systems review, we trace the data flows, understand the business processes, analyze current protections in relation to regulatory frameworks/regulatory compliance, compare against best practices within peer organizations, and provide recommendations and remediation plans that align with strategic goals.
While we apply experiences from every prior cyber assessment we’ve done, we believe each one is unique to an organization and should be driven by the risk categories an organization prioritizes the most. These typically are:
- Compliance – risk tied to violation of laws or regulations, or internal policies & procedures
- Operational – risk associated with failed internal processes, people or systems, or externally-driven processes
- Transactional – risk related to problems delivering a product or service
- Reputational – risk tied to negative public opinion of your organization
- Strategic – risk of inappropriate decision making that leads to an organization’s inability to meet its primary goals
The report we deliver following an assessment will inform organizations of their cybersecurity posture, recommend detailed and prioritized action for improvement, and provide a path for long-term sustainability of lower risk levels. At a minimum, our objective is to identify security weaknesses and risks that may have been overlooked during an internal analysis. These are oversights that often lead to the biggest, most expensive and reputation-harming security incidents.
Business Process Analysis
Organizations waste considerable time and money trying to rid themselves of inefficiencies and redundant work. One example is switching to a new software in hopes that underlying problems disappear. Software changes alone rarely are capable of this. To make matters worse, changes are often made in isolation, with a narrow, intra–departmental focus instead of a cross-organizational view. These “fixes” can benefit one area of the company but end up having no positive impact on other areas (or even a negative impact).
A more thorough analysis of end-to-end business processes can reveal much about the root causes of problems with productivity and efficiency levels. When doing a technology assessment, we always look at existing process flows and how they impact business results. These are the areas we typically focus on along with examples of how we can assist:
- Finance – Identifying where costs can be lowered, such as through software tools and service-based technologies to reduce bloated spending and eliminate manually-intensive workflows
- Operations – Restructuring repetitive, paper-based processes to reduce costly errors and redeploy people to higher-value roles
- Employee productivity & talent retention – Determining where time is being unnecessarily wasted and employee morale is suffering due to technology limitations
- Customer service – Evaluating current customer service processes to understand how the customer experience can be enhanced by automating support tasks and improving customer-facing systems

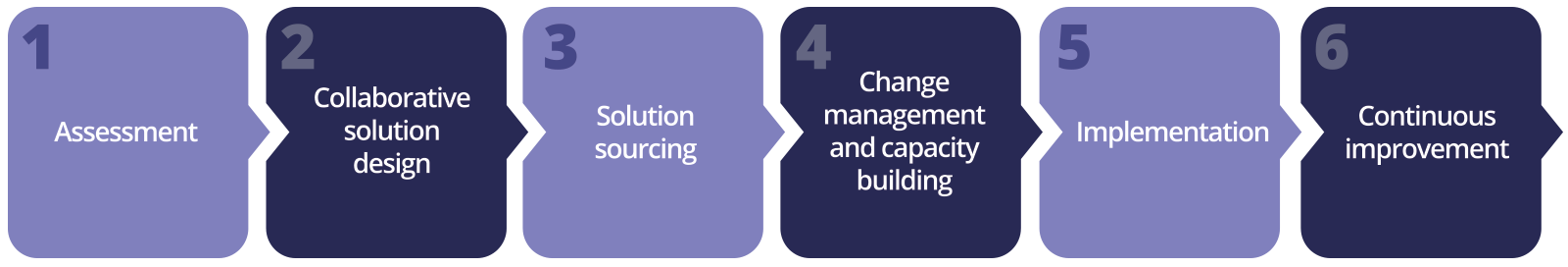
 “Our consultative approach focuses on four main pillars of success; reliability, usability, security, and sustainability. Our goal is to ensure organizations have a strategy to achieve transformation in all four areas and have a structure for continuous monitoring and improvement. Transformation is a journey that encompasses more than just technology components, it’s about culture, efficiency, capacity building and organizational change; it’s our passion as transformative experts to help guide you through this process.”
“Our consultative approach focuses on four main pillars of success; reliability, usability, security, and sustainability. Our goal is to ensure organizations have a strategy to achieve transformation in all four areas and have a structure for continuous monitoring and improvement. Transformation is a journey that encompasses more than just technology components, it’s about culture, efficiency, capacity building and organizational change; it’s our passion as transformative experts to help guide you through this process.”